最新发布|DACS-Gaming游戏行业解决方案重磅升级
了解更多DataCloak Launches HyperCloak® – China’s First Enhanced Zero Trust Security Architecture
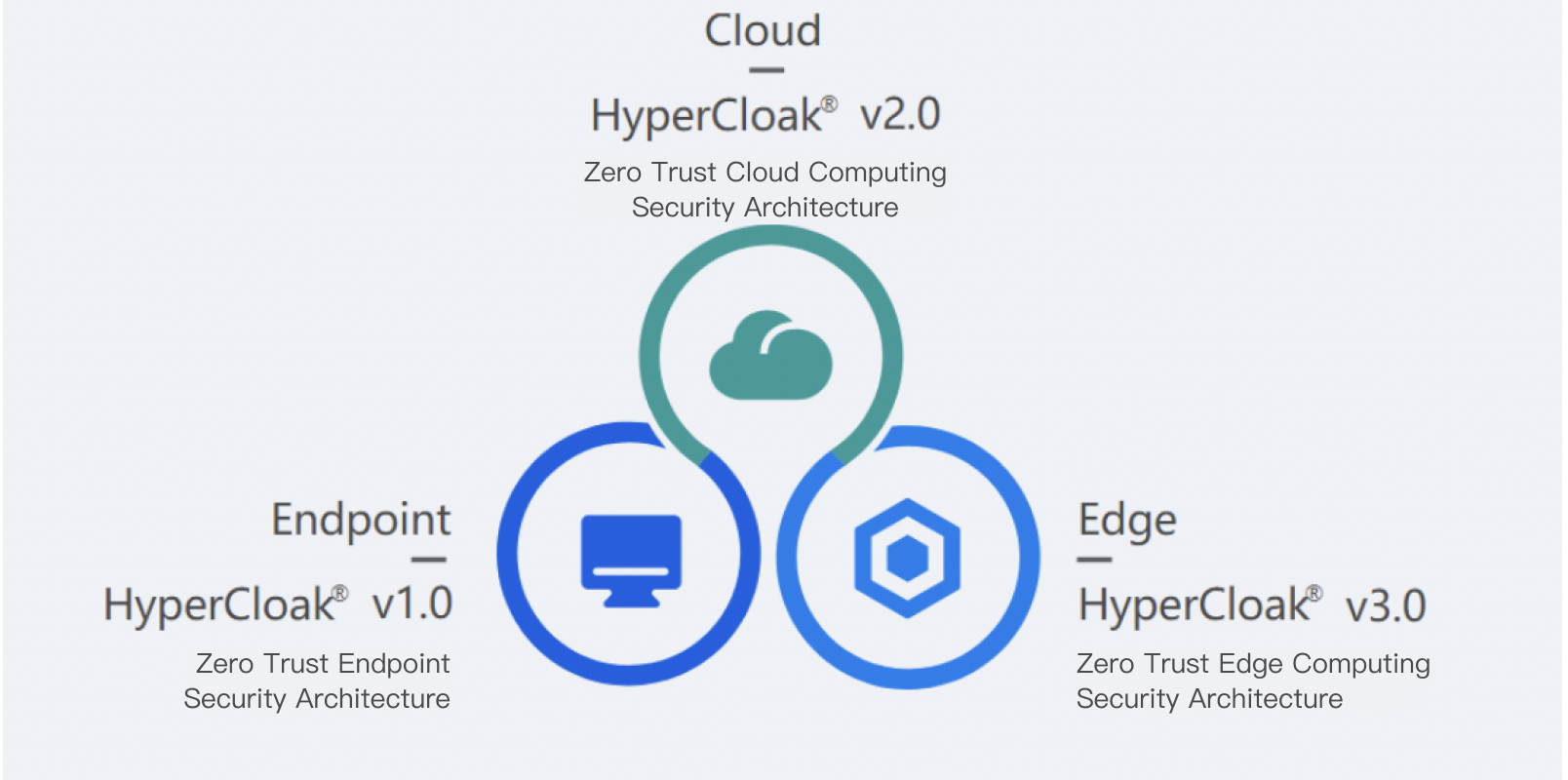
DataCloak officially launched HyperCloak® – an enhanced zero trust security architecture – at the "2020 ZTAT Summit" on September 4, 2020. HyperCloak® optimized the deficiencies of the ZTNA zero trust security architecture represented by Google BeyondCorp in terms of data security, protocol support and implementation difficulties. At the same time, it opened up the corresponding security capabilities and SDK, which can deeply collaborate with existing products in enterprises and industries to jointly promote the upgrade of enterprise IT network security infrastructure and digital transformation.
The current mainstream ZTNA zero trust security architecture applies fine-grained access control technology based on the identity of personnel and devices, which basically solves the problem of secure access to "borderless" enterprise resources. However, at the same time, it also introduces new problems such as the risk of border expansion, limited support for application protocols, and high transformation costs, etc. While the ZTNA framework solves network access security (network border) and "borderless" access to enterprise resources in an open environment, it also allows enterprise digital assets to be more widely distributed, and the security of enterprise digital assets at the edge and endpoints is a major problem. ZTNA framework in the network application layer to exert control, often only to support a limited number of application protocols, such as http/https, SSL, FTP, etc., which makes its application scope is greatly restricted; ZTNA framework relies on the deep transformation of enterprise applications, business migration costs are high and difficult to implement.
DataCloak believes that zero trust is a concept which strives to ensure that legal owners or applications receive proper authorization and protect enterprise assets in an open network environment. Based on the ZTNA architecture, solving the problem of zero trust concept implementation with the perspective of security as infrastructure will greatly simplify the complexity of this process.
HyperCloak®, an enhanced zero trust architecture with more comprehensive security capabilities, wider coverage, and more accessible implementation, upholds the security-as-infrastructure concept and has the following key characteristics:
- Integration of lightweight trusted computing and the zero trust concept to establish a reliable fundamental workspace
- Realize the security control capability of terminal data computing and storage through the new generation sandbox technology at the terminal
- Provide 3 to 7-layer encrypted communication and fine-grained access control capabilities on the network
- Widely support various network communication protocols to comprehensively cover various application scenarios of enterprises
- Provide fine-grained SDP (Software Defined Perimeter) capability, and build software-defined end-to-end enterprise security boundaries together with terminal security sandbox
- Deep integration with the operating system kernel and underlying infrastructure, transparent to upper-layer applications, and can be upgraded to a zero trust network security architecture without application modification
DataCloak Launches HyperCloak® – China’s First Enhanced Zero Trust Security Architecture
DataCloak officially launched HyperCloak® – an enhanced zero trust security architecture – at the "2020 ZTAT Summit" on September 4, 2020. HyperCloak® optimized the deficiencies of the ZTNA zero trust security architecture represented by Google BeyondCorp in terms of data security, protocol support and implementation difficulties. At the same time, it opened up the corresponding security capabilities and SDK, which can deeply collaborate with existing products in enterprises and industries to jointly promote the upgrade of enterprise IT network security infrastructure and digital transformation.
The current mainstream ZTNA zero trust security architecture applies fine-grained access control technology based on the identity of personnel and devices, which basically solves the problem of secure access to "borderless" enterprise resources. However, at the same time, it also introduces new problems such as the risk of border expansion, limited support for application protocols, and high transformation costs, etc. While the ZTNA framework solves network access security (network border) and "borderless" access to enterprise resources in an open environment, it also allows enterprise digital assets to be more widely distributed, and the security of enterprise digital assets at the edge and endpoints is a major problem. ZTNA framework in the network application layer to exert control, often only to support a limited number of application protocols, such as http/https, SSL, FTP, etc., which makes its application scope is greatly restricted; ZTNA framework relies on the deep transformation of enterprise applications, business migration costs are high and difficult to implement.
DataCloak believes that zero trust is a concept which strives to ensure that legal owners or applications receive proper authorization and protect enterprise assets in an open network environment. Based on the ZTNA architecture, solving the problem of zero trust concept implementation with the perspective of security as infrastructure will greatly simplify the complexity of this process.
HyperCloak®, an enhanced zero trust architecture with more comprehensive security capabilities, wider coverage, and more accessible implementation, upholds the security-as-infrastructure concept and has the following key characteristics:
- Integration of lightweight trusted computing and the zero trust concept to establish a reliable fundamental workspace
- Realize the security control capability of terminal data computing and storage through the new generation sandbox technology at the terminal
- Provide 3 to 7-layer encrypted communication and fine-grained access control capabilities on the network
- Widely support various network communication protocols to comprehensively cover various application scenarios of enterprises
- Provide fine-grained SDP (Software Defined Perimeter) capability, and build software-defined end-to-end enterprise security boundaries together with terminal security sandbox
- Deep integration with the operating system kernel and underlying infrastructure, transparent to upper-layer applications, and can be upgraded to a zero trust network security architecture without application modification

Contact Us