最新发布|DACS-Gaming游戏行业解决方案重磅升级
了解更多Data Classification Management, Software Defined Perimeter
Enterprise data cannot not confined to a single secure workspace and cannot flow. DataCloak believes the nature of data is to flow, as data can only maximize its value through flowing. Based on this, DACS provides secure data flowing and sharing capabilities. Data flows through secure encrypted tunnels between different secure workspaces. These software-defined secure tunnels have the following characteristics:
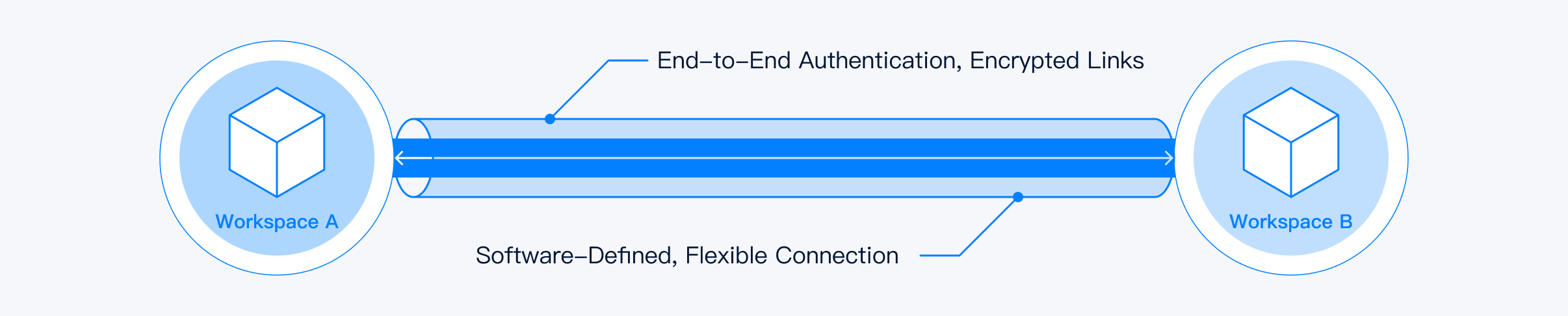
- Two-way authentication links and end-to-end encryption to ensure data transmission security
- Virtualized network tunnels and WAN network penetration capabilities to ensure global accessibility and instant availability
- Software-defined, flexible connection, and fine-grained controlled network boundaries can perfectly match enterprise businesses and data life cycles
Data classification management and securely flow
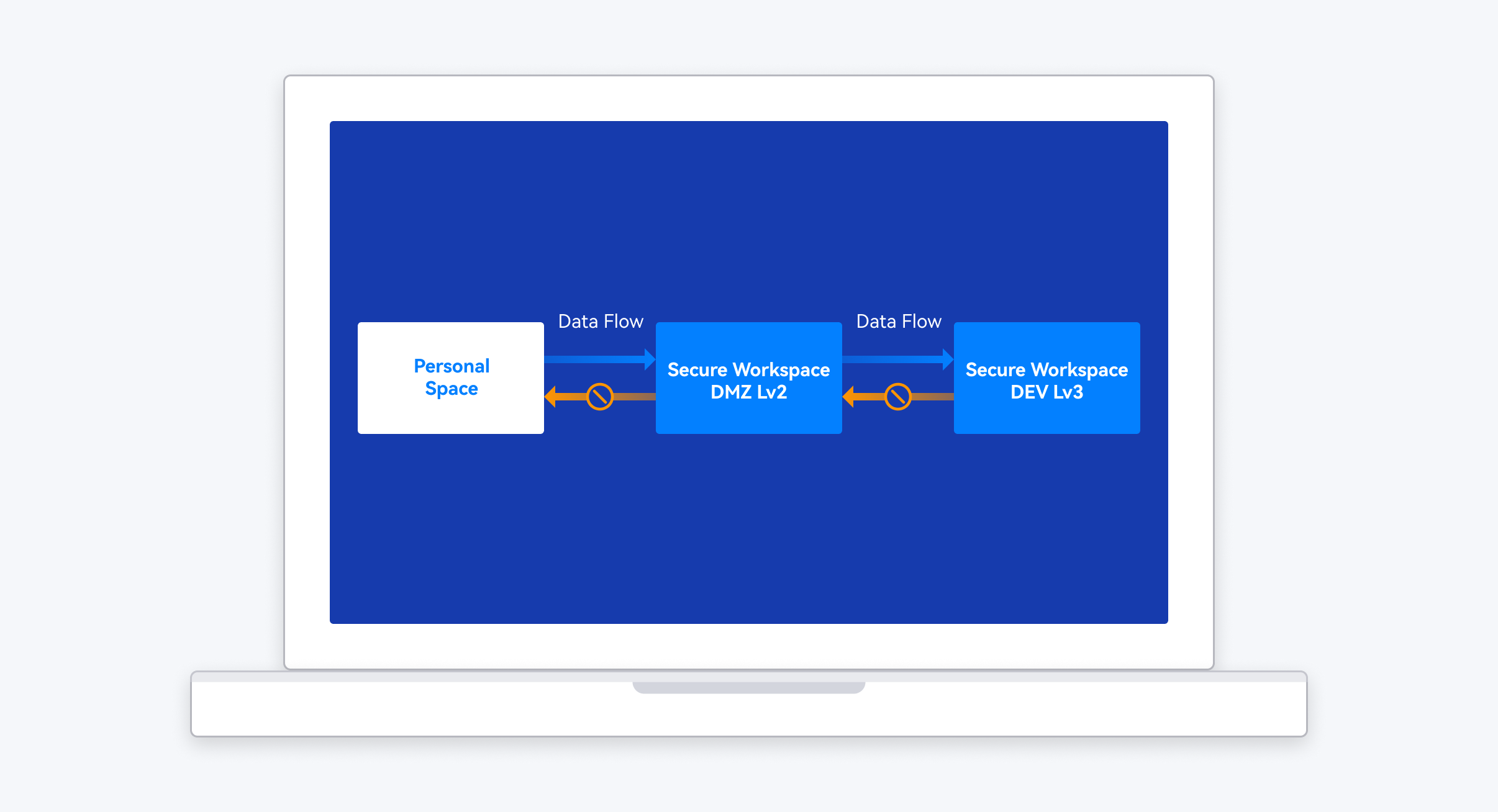
DataCloak innovates the concept of data classification management. Based on the different importance of enterprise business and data, the secure workspace is custom set from high to low security level, such as protecting code management tools like SVN and Git and important code data in the workspace with high security level, and protecting OA software tools and sensitive office file data in the workspace with low security level. It also supports setting different security control policies for each secure workspace according to different security levels, allowing enterprises to achieve more accurate and detailed data security control.
By default, the higher the security level, the stricter the security policy. Enterprise data follow the principle of "one-way flow" on each terminal device, only allowing data transfer from low security level to high, and the opposite is not possible.
Furthermore, DACS Pro supports the secure workspace isolation function. After enabling this function, data cannot be flowed between different secure workspaces without approval.
Secure data sharing
Between different terminals of different users, enterprise data can be securely shared within a security domain composed of multiple secure workspaces. Users can share specified enterprise documents to other specified users within the security domain, and when the shared users receive the documents, they are only allowed to download them to the corresponding secure workspace, still ensuring that the data is used and stored within the trusted computing environment. This effectively ensures that data is shared and flowed within the software-defined security boundary, and effectively avoids cross-level leakage of data, even leaked to personal environments and the Internet. At the same time, the whole process of data flow and sharing is monitored and audited by the management platform.
Secure outgoing of data
In daily work, enterprises often need to share data with third parties or people outside the organization. DACS Pro fully considers the scenario of data outgoing, supporting short-term outgoing, long-term outgoing, and email outgoing, etc. Combined with the multi-level approval mechanism, users can initiate document outgoing applications and submit the document in the secure workspace. Administrators can view the content of the outgoing documents, and only after the approval, the user is allowed to send the enterprise documents to third parties outside the secure workspace. The entire outgoing process and the content of the outgoing documents are audited and recorded to ensure that there is evidence to be found and relied on afterwards.
Data Classification Management, Software Defined Perimeter
Enterprise data cannot not confined to a single secure workspace and cannot flow. DataCloak believes the nature of data is to flow, as data can only maximize its value through flowing. Based on this, DACS provides secure data flowing and sharing capabilities. Data flows through secure encrypted tunnels between different secure workspaces. These software-defined secure tunnels have the following characteristics:

- Two-way authentication links and end-to-end encryption to ensure data transmission security
- Virtualized network tunnels and WAN network penetration capabilities to ensure global accessibility and instant availability
- Software-defined, flexible connection, and fine-grained controlled network boundaries can perfectly match enterprise businesses and data life cycles
Data classification management and securely flow
DataCloak innovates the concept of data classification management. Based on the different importance of enterprise business and data, the secure workspace is custom set from high to low security level, such as protecting code management tools like SVN and Git and important code data in the workspace with high security level, and protecting OA software tools and sensitive office file data in the workspace with low security level. It also supports setting different security control policies for each secure workspace according to different security levels, allowing enterprises to achieve more accurate and detailed data security control.
By default, the higher the security level, the stricter the security policy. Enterprise data follow the principle of "one-way flow" on each terminal device, only allowing data transfer from low security level to high, and the opposite is not possible.
Furthermore, DACS Pro supports the secure workspace isolation function. After enabling this function, data cannot be flowed between different secure workspaces without approval.

Secure data sharing
Between different terminals of different users, enterprise data can be securely shared within a security domain composed of multiple secure workspaces. Users can share specified enterprise documents to other specified users within the security domain, and when the shared users receive the documents, they are only allowed to download them to the corresponding secure workspace, still ensuring that the data is used and stored within the trusted computing environment. This effectively ensures that data is shared and flowed within the software-defined security boundary, and effectively avoids cross-level leakage of data, even leaked to personal environments and the Internet. At the same time, the whole process of data flow and sharing is monitored and audited by the management platform.
Secure outgoing of data
In daily work, enterprises often need to share data with third parties or people outside the organization. DACS Pro fully considers the scenario of data outgoing, supporting short-term outgoing, long-term outgoing, and email outgoing, etc. Combined with the multi-level approval mechanism, users can initiate document outgoing applications and submit the document in the secure workspace. Administrators can view the content of the outgoing documents, and only after the approval, the user is allowed to send the enterprise documents to third parties outside the secure workspace. The entire outgoing process and the content of the outgoing documents are audited and recorded to ensure that there is evidence to be found and relied on afterwards.
Contact Us